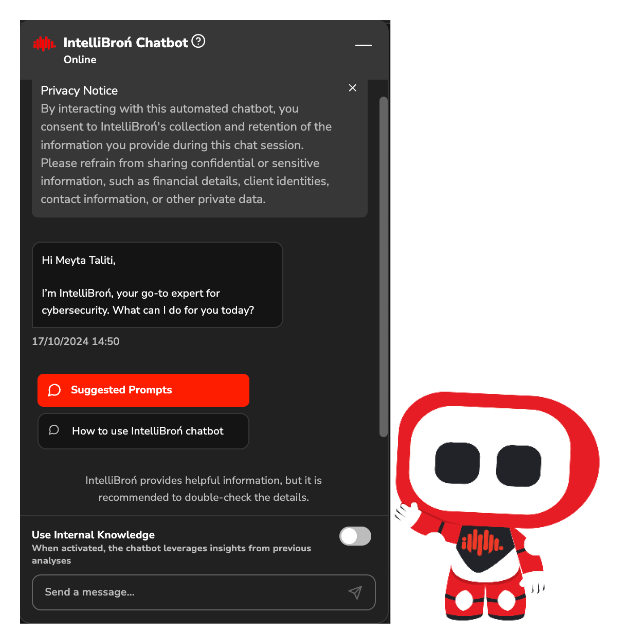
AI — Chatbot with RAG (Retrieval-Augmented Generation)
This article shows how IntellIBroń ChatBot AI technology works in the backend. We utilise our own developed RAG. Retrieval-Augmented Generation (RAG) is a technique that combines retrieval-based and generative methods to produce more accurate and relevant responses.